These days, hiding or locking a folder or file is probably something you will need if you use a computer that others use too.
Let me introduce the 5 Ways to Lock Or Hide A Folder, A File Or A Drive On The Computer.
Method 1 (the easy one)
1. Click “Start”, “Run,” and then type cmd. When the command prompt opens type “CD C:\Test” (replace “Test” with the name of the folder you want to hide.)
2. Now type “attrib file +s +h” and replace “file” with the name of the actual file name you would like to hide.
3. Now, go back to C:\Test and look for your file or folder, it’s not there! You cannot find it through simply browsing around, through the command prompt, or even if you click “Show Hidden Files and Folders”.
4. To find the folder and it’s contents again simply go back to the command prompt, type “CD C:\Test” (of course, again replacing “Test” with the name of the folder,) and then type “attrib filename -s -h”. You should now be able to find your file again!
Method 2 (this is where it starts to get slightly more difficult)
This method, unlike the previous one, hides an entire drive instead of individual files or folders:
(Before you ever use the registry I HIGHLY RECOMMEND backing up your registry with a tool similar to Registry Tool or CCleaner. You may as well use a manual method similar to this.)
1. Go to “Start,” “Run,” and type regedit.
2. When the registry editor loads, navigate to: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\
Policies\Explorer
3. Right click on “Explorer” and select “New” and “DWORD Value.”
4. Name the value NoDrives and select “Decimal” as the base.
5. In the value type the number that corresponds with the drive below:

(E.g. If you would like to hide drive E, type 16. You may also hide multiple drives by adding the two numbers. E.g. If you would like to hide drives E and G, 16+64=80.)
6. Now, after you restart your computer, you should not be able to see the drive.
Method 3
1. Create a folder in a drive for easy access, e.g. C:. (Name it something related to the Control Panel, e.g. Users.)
2. Create a new file in Notepad and copy and paste the following into it:
ren Users Users.{21EC2020-3AEA-1069-A2DD-08002B30309D}
3. Replace “Users” with the name of the folder you created and save the file as loc.bat.
(You should now be able to see your folder and the loc.bat file, with the loc.bat in the same directory as the folder Not in it.)
4. Now, right-click and create another text file. Copy and Paste the following into it:
ren Users.{21EC2020-3AEA-1069-A2DD-08002B30309D} Users
(Make sure to replace the word “Users” with the name of your folder.)
5. Save it as key.bat.
6. Now you should see the loc.bat and the key.bat files in the same directory as the folder you created.
7. Now, all you need to do is double-click on the loc.bat file and the folder should have an icon that looks like the control panel. If you click on the folder it should redirect you to the Control Panel and thus you have locked the folder.
8. Of course, to unlock it, simply double-click on the key.bat file and the folder should turn back into the folder you first created.

Method 4
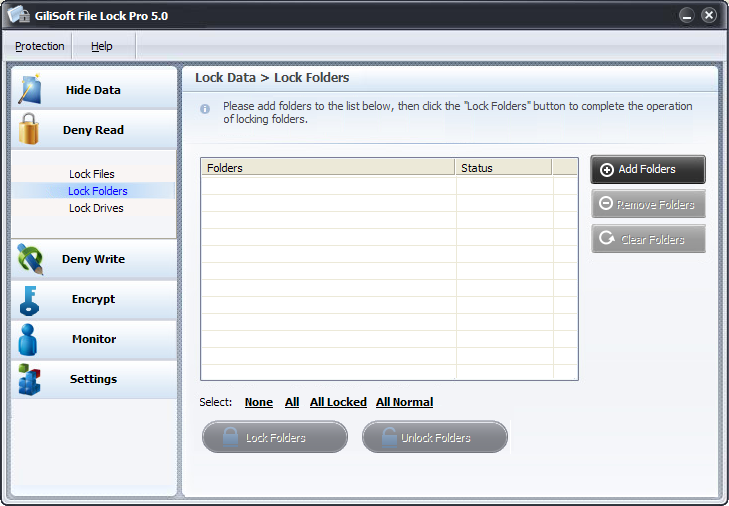
Use GiliSoft File Lock Pro or GiliSoft File Lock to hide or lock any your files ,folders,drives on your computer.
Method 5
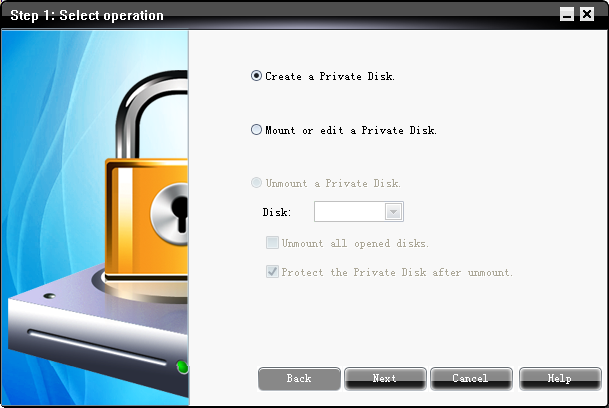
Use GiliSoft Private Disk to create a virtual encryption disk to save your important files.
.png) With GiliSoft File Lock you can easily protect any number of folders and files on your computer. You can select any file or folder to protect from the program, or protect the file or folder using Windows Explorer context menu.
Features and benefits
With GiliSoft File Lock you can easily protect any number of folders and files on your computer. You can select any file or folder to protect from the program, or protect the file or folder using Windows Explorer context menu.
Features and benefits